‘Sup PSHomies,
This is me every single time I sit down to use Pester…

Hehe…
While I do enjoy using Pester for operational validation, what do you do with the ones that fail? Most of the time you’re the one doing the validation in the chain of process and everything goes right! Because you’re that good… 😉 Hehe… I’ve been recently asked to update some users where some attributes didn’t get populated during a migration… Are you thinking what I’m thinking? 😉
The first thing I did was export the attributes they needed, easy enough. Next was to change the necessary attributes to the correct value. The ones that differ will fail (Of course they will Urv, not a total retard here… get on with it… )
Here’s where having proper descriptions can go a long way.
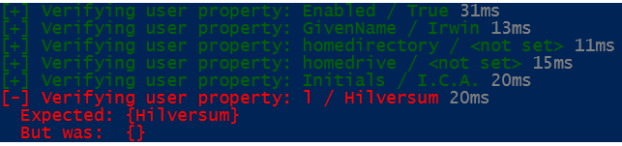
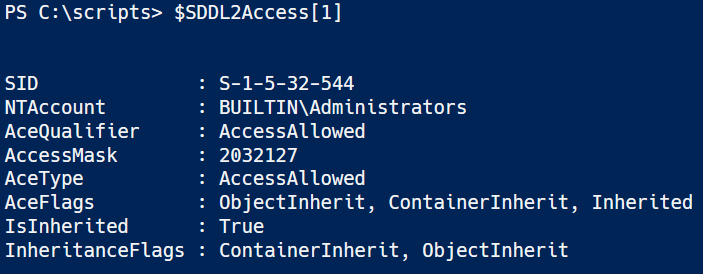
This is what a Test ErrorRecord looks like when you capture the results: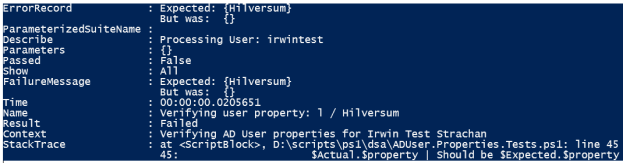
At first I thought of using regex on the ErrorRecord. Some of the attributes aren’t set which gave me some issues, so I decided to breadcrumb the name. First do a split on the colon ‘:’ grab the last part and do a split again using ‘/’ to get the attribute name and value. Don’t forget to trim() 🙂
There were some other Attributes that weren’t part of the default parameter set of the Set-ADUser cmdlet. To change those attributes you need to use the DisplayName and the Replace Operator. For the attributes “not set” that need to be cleared, use the Clear operator. Just don’t use both the parameter and the DisplayName! I had EmailAddress and mail in the CSV file, one passed and the other failed… I got rid of mail…
Ok here’s the code to get things done:
First get failed Pester tests.
| <# | |
| Author: I. Strachan | |
| Version: | |
| Version History: | |
| Purpose: Validate AD User attributes | |
| #> | |
| [CmdletBinding(SupportsShouldProcess = $True)] | |
| Param( | |
| $csvFile = 'd:\scripts\ps1\source\csv\SetUser.csv' | |
| ) | |
| #region Import Csv file | |
| $csvUsers = Import-Csv -Path $csvFile -Delimiter "`t" -Encoding UTF8 | |
| $userProperties = ($csvUsers | Get-Member -MemberType NoteProperty).Name | | |
| Where-Object {$_ -ne 'OU'} | |
| #endregion | |
| #region Main | |
| $csvUsers | | |
| Foreach-Object { | |
| $Expected = $_ | |
| Describe "Processing User: $($Expected.SamAccountName)" { | |
| Context "Verifying AD User properties for $($Expected.DisplayName)" { | |
| #Get AD user properties | |
| $Actual = Get-ADUser -Identity $Expected.SamAccountName -Properties $userProperties | |
| ForEach( $property in $userProperties){ | |
| if (([string]::isNullOrEmpty($Expected.$property))) { | |
| $Expected.$property = $null | |
| $lableExpected = '<not set>' | |
| } | |
| else{ | |
| $lableExpected = $Expected.$property | |
| } | |
| it "Verifying user property: $($property) / $($lableExpected)"{ | |
| $Actual.$property | Should be $Expected.$property | |
| } | |
| } | |
| } | |
| } | |
| } | |
| #endregion | |
| #Run PesterTest and save results | |
| $resultsTest = Invoke-Pester D:\scripts\ps1\dsa\ADUser.Properties.Tests.ps1 -PassThru | |
| #Get All failed tests | |
| $failedTests = $resultsTest.TestResult.where{$_.Passed -eq $false} | |
| $failedTests | | |
| ForEach-Object{ | |
| $result = $_.Name.Split(':')[-1] | |
| $arrResult = $result.Split('/') | |
| [PSCustomObject]@{ | |
| SamAccountName = ($_.Describe.split(':').Trim())[-1] | |
| Property = $arrResult[0].Trim() | |
| Expected = $arrResult[1].Trim() | |
| } | |
| } -OutVariable failedObjects | |
| #Export Failed objects | |
| $failedObjects | | |
| Export-Csv -Path D:\Scripts\ps1\source\csv\FailedTests.csv -Delimiter "`t" -NoTypeInformation -Encoding UTF8 |
This will give me a csv file with the following Columns, SamAccountName, Property & Expected (Value).
The set failed Pester tests will either set or clear the attribute depending on it’s value. If it’s $null it will be cleared.
| <# | |
| Author: I. Strachan | |
| Version: | |
| Version History: | |
| Purpose: Set ADUser attributes of failed tests | |
| #> | |
| [CmdletBinding(SupportsShouldProcess = $True)] | |
| Param( | |
| $csvFile = 'D:\Scripts\ps1\source\csv\FailedTests.csv' | |
| ) | |
| $FailedTests = Import-Csv -Path $csvFile -Delimiter "`t" -Encoding UTF8 | |
| #Get Set-ADUser Parameters | |
| $setADUserParameters = (Get-Command Set-ADUser).ParameterSets.Parameters.Where{ $_.IsDynamic -eq $true} | Select-Object -ExpandProperty Name | |
| #Get User Property | |
| $FailedTests | | |
| Foreach-object{ | |
| #Set Expected to null if <not set> | |
| $Expected = @{$true = $null; $false = $_.Expected}[$_.Expected -eq '<not set>'] | |
| If ($setADUserParameters.Contains($_.Property)){ | |
| $paramSetADUser = @{ | |
| Identity = $_.SamAccountName | |
| $_.Property = $Expected | |
| } | |
| Set-ADUser @paramSetADUser | |
| } | |
| else{ | |
| if($Expected){ | |
| Set-ADUser -Identity $($_.SamAccountName) -Replace @{$_.Property = $Expected} | |
| } | |
| else{ | |
| Set-ADUser -Identity $($_.SamAccountName) -Clear $($_.Property) | |
| } | |
| } | |
| } |
Here are some screenshots to give you an idea what to expect.
Ideally you’d only have a few failed tests. I wouldn’t use this to reset entire User attributes. Moving and/or renaming an object isn’t supported… yet! 😉
So there you have it, taking failed Pester tests values and setting them accordingly!
Hope it’s worth something to you,
Ttyl,
Urv




































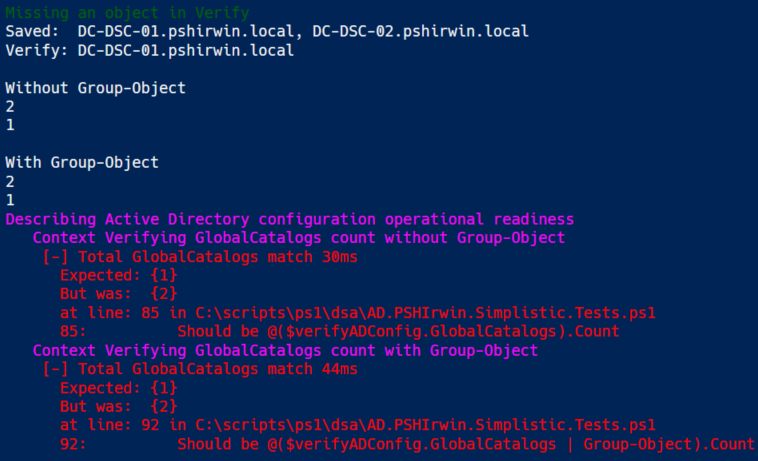
 This is an odd test, it could be a typo. Imagine having a list where double entries aren’t that obvious, this should catch it. Now ideally you’d use your source code that you used during deployment. I’m assuming you did automate your process eh? 😉 Without the Group-Object the count is identical. With Group-Object you only have one entry! This could explain an exception happened during deployment… Accidents will happen…
This is an odd test, it could be a typo. Imagine having a list where double entries aren’t that obvious, this should catch it. Now ideally you’d use your source code that you used during deployment. I’m assuming you did automate your process eh? 😉 Without the Group-Object the count is identical. With Group-Object you only have one entry! This could explain an exception happened during deployment… Accidents will happen…








